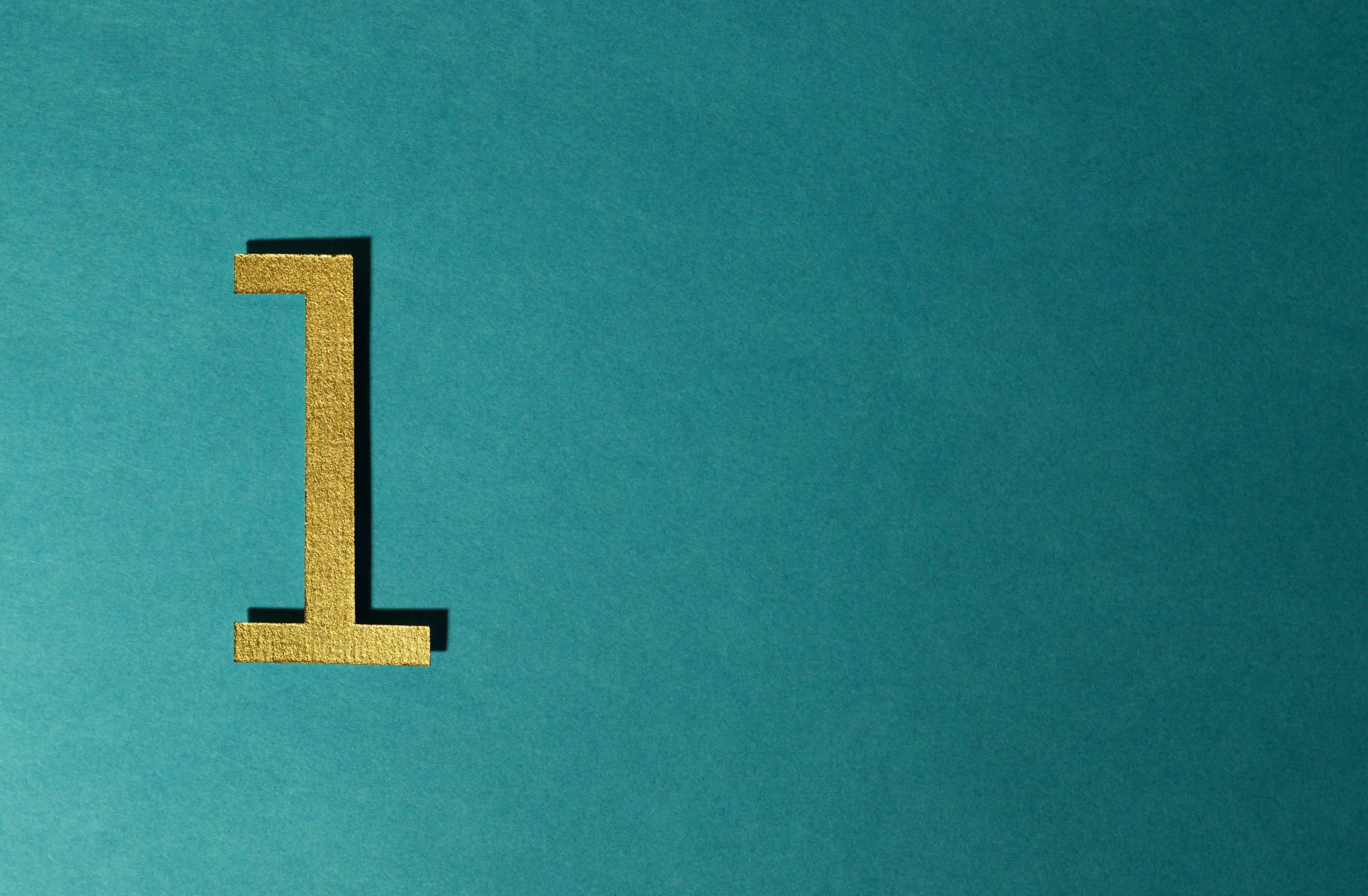We’ve said it before, and we’ll repeat it again; in some ways, cybersecurity is in permanent beta. The threats and challenges are constantly evolving, and no organization, institution or business is 100% secure forever. Cybersecurity is never really ‘finished.’ It’s an ongoing process with important milestones along the way. You can’t order it in a pre-packaged box online, it takes time and effort to develop a program specific to your needs.
With that said, security program development (i.e. creating a cybersecurity posture for your distinct needs) typically follows four key phases for most organizations, each one building on the last. Over the coming months, we’ll be crafting a blog post specific to each stage. We’re looking at the initial stage, or the foundational phase, for this post.
Initial Phase of Security Program Development
Every small to medium-sized business presents its own set of challenges and opportunities. Business owners are often pulled in a wide variety of different directions daily. For many, developing a robust cybersecurity posture is relatively low on the priority list. It isn’t that these business owners don’t care about securing their intellectual property or their customers’ data, but rather, they’re rushed off their feet and don’t really know where to begin. It’s something that they’ll get to next week when things settle down a bit (FYI – this rarely happens! Just saying).
In this environment, businesses often grow with ad hoc IT and little in the way of proper IT management. If this sounds familiar, you’re not alone. We work with many organizations and have seen it all over the years. So if you’re in this boat, where do you start?
Start here
While it might not seem to be directly security-related, implementing some common formal IT management best practices goes a long way towards improving overall security posture. An excellent place to begin is by developing an inventory of critical IT and information assets. What are you working with, and what are your essential information assets — i.e. what do you need to function?
Once that is done, the next step involves documenting all IT operational procedures. The ‘what happens if I get hit by a bus next week?’ backup plan. Granted, it isn’t a nice thing to think about, so let’s put it another way — what happens if you want to take a vacation to the Bahamas? Better to document those procedures so you can easily onboard new team members and also have a good handle on your information technology policies and procedures.

The following items on your agenda will be backups and patching. With backups, you want to be backing up your key data and information infrastructure. With patching, you’re plugging gaps, performing updates and eliminating any obvious security vulnerabilities (weak passwords, outdated software, that kind of thing). This is an ongoing process, and you’ll need to be doing backups and patching periodically.
Following that, you want to ensure you have your key foundational technical security controls in place. This refers to things such as desktop security (‘anti-virus’, personal firewall etc.) and network perimeter security. We recommend you look at all the security controls included as part of Implementation Group 1 in the CIS Critical Security Controls for extra assurance.
We know… It’s all exciting stuff, said no one ever, but if your data security needs never cause your heart to race, that’s probably a good thing overall. With that said, it’s vital and only becoming more relevant with each passing day. At SeekingFire, we can help guide you through this work to ensure you have the appropriate security foundations in place.
Indeed, once you’ve got your IT operating correctly, consider having a third party (like SeekingFire!) perform vulnerability assessment scans of your IT periodically so that your new and shiny IT management practices can remediate any vulnerabilities discovered. Essentially, we’ll probe and test and report back to help ensure that your intellectual property and the data of your customers is well protected.

This will put your initial security phase in a strong place and ensure you have the right foundations for your organization’s cybersecurity needs. From there, you can begin building into the Security Program Planning phase, but more on that next time.
Before we go
At SeekingFire Consulting Inc., we’re proud to work with clients across Western Canada on their data security needs. If you’re a small to medium-sized business operating online/in a digital space, you can likely benefit from our suite of services. We offer free consultations to all prospective clients and are happy to meet you where you are at. If you would like to learn more, please reach out.
Disclaimer
While we have made every effort to present accurate, unbiased and helpful information in this article, please note that it reflects the author’s opinion and is written for the purposes of general knowledge, information and discussion. This article is not intended as legal advice, nor should it be considered as advice specific to your individual data security situation. If you would like to discuss your cybersecurity needs in specific detail, please get in touch with us.